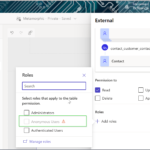
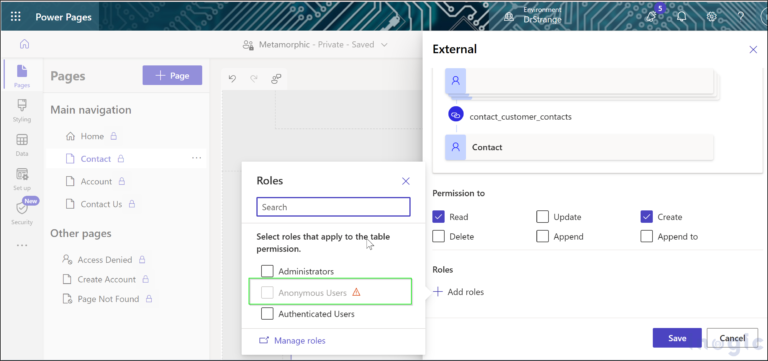
One of the remarkable features of Salesforce is its versatile, multi-layered sharing system that lets you assign different data sets to different sets of users. This not only minimizes the risk of data misuse but also streamlines data access for users.
As organizations increasingly embrace Salesforce’s Experience Cloud, it becomes crucial to grasp the tools and techniques for managing user permissions and data access. This article delves into permission sets, profiles, and security best practices to ensure your site’s security and efficient data management.
Understanding Data Access in Salesforce
Managing data access and user permissions is a vital aspect of any Salesforce Experience Cloud site. Without proper organization, users may struggle to obtain relevant data or gain unauthorized access. Before exploring effective methods for user permissions and data access, let’s examine the levels of data access in Salesforce.
- Organization. Control access for the entire organization, including time and geographical restrictions for approved users.
- Objects. Regulate access to specific records within objects, such as accounts or contacts, by setting object-level permissions.
- Records. Control access to specific records based on user profiles or roles using sharing rules and role hierarchy.
- Fields. Manage user visibility, and edit, and delete permissions for specific fields within an object.
Did you know that Salesforce has recently announced a significant change to the data access and user permission management in Salesforce? The company has reported the end-of-life of permissions on profiles, which will take effect in the Spring ’26 release. Get more details here: The Future of User Management in Salesforce: Switching From a Profile-Based Access Approach to Permission Sets.
![]() Don’t forget to check out: Idea Management on Experience Cloud: Transforming Business Innovation
Don’t forget to check out: Idea Management on Experience Cloud: Transforming Business Innovation
Managing user permissions in Salesforce Experience Cloud
In Salesforce Experience Cloud, user permissions are managed through profiles and permission sets.
- Profiles define user access levels to various Salesforce objects and fields. Customize profiles to assign varying access levels to different users, simplifying system-wide changes.
- Permission sets allow additional permissions beyond profile allowances. Grant specific object or field access without changing users’ profiles.
To control user access to your Experience Cloud site:
- Authenticated users. Manage access for authenticated users through profiles and permission sets, facilitating site membership management.
- Guest users. For external users, configure guest user profiles and set site access to public pages and content.

Top 5 Best Practices for Secure Data Access in Experience Cloud Sites
- Regularly review and update user permissions. Keep sensitive data accessible only to those who need it by regularly reviewing and updating user permissions.
- Keep your site up-to-date. Ensure your Experience Cloud site and third-party applications are up-to-date with the latest security patches and updates.
- Monitor and audit user activity. Detect and respond to suspicious activities by using Salesforce’s built-in logging and reporting tools.
- Limit guest user data access. Restrict guest users to necessary data by creating sharing rules for access without login credentials.
- Train employees on security best practices. Educate employees on security best practices to enhance organizational security awareness.
![]() Check out another amazing blog here by Advanced Communities: SEO for Salesforce Experience Cloud Websites: Best Practices
Check out another amazing blog here by Advanced Communities: SEO for Salesforce Experience Cloud Websites: Best Practices
For expert assistance, turn to professionals: If you encounter challenges with Salesforce portals or Experience Cloud sites, consider seeking assistance from Advanced Communities. With extensive experience in Salesforce Experience Cloud development and implementation, we are well-equipped to address your needs effectively.